
Powerful email encryption with Frama RMail
Advanced email security: TLS and E2E encryption
Trustworthy Communication Thanks to Secure Encryption
The efficacy of any encryption service depends on the ease-of-use for the recipient. Frama RMail provides robust encryption and a user-friendly experience for both the sender and the receiver. Our solution ensures that your sensitive data remains seure and inaccessible to unauthorised individuals both during transit and when it gets to its destination. .
Data protection and confidentiality with Frama RMail
Registered encryption for secure communication
Most emails contain sensitive or 'personally identifiable' information, meaning that it is a GDPR breach should they fall into the wrong hands. Frama Rmail's features ensure that only authorised persons have access to the content of your emails. With the proof of delivery that Frama RMail provides, you can demonstrate the encryption strength and method of encryption used, making 'due dili=gence' when it comes to GDPR and other industry-sepcific regulation simple and seamless.
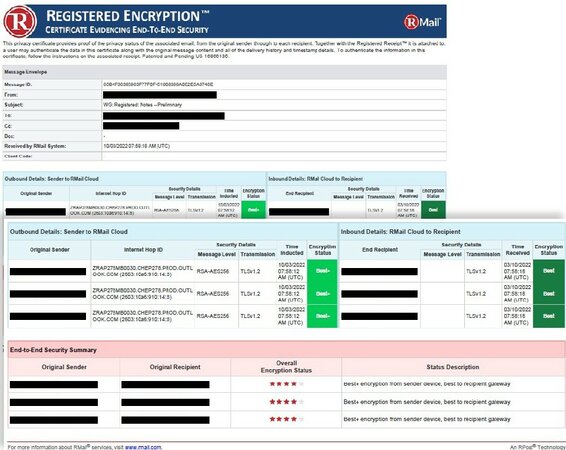
Maximum security against fraud and cybercrime
Encryption in conjunction with Frama Rmail
Emails sent in the normal way are an easy target for cybercriminals. Frama RMail protects your digital communications with reliable, provable encryption. Additionally, Frama's Pre-Crime extension ensures continuous monitoring of your emails to detect and defend against multiple attack scenarios.
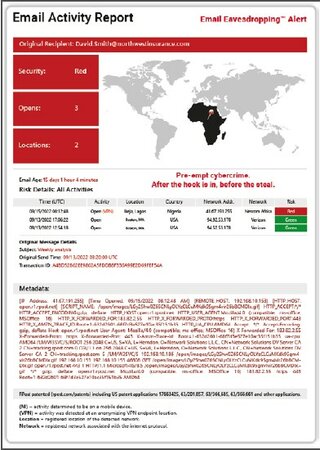
Comprehensive protection against eavesdropping and email interception
Powerful encryption with Frama RMail
Without proper encryption, emails are notoriously vulnerable during their transmission. Frama RMail offers robust encryption that makes it virtually impossible for cybercriminals to decrypt the data contained within an email. Frama RMail uses bleeding-edge technologies such as TLS1.3 or AE256bit encryption to protect your data, on any device.
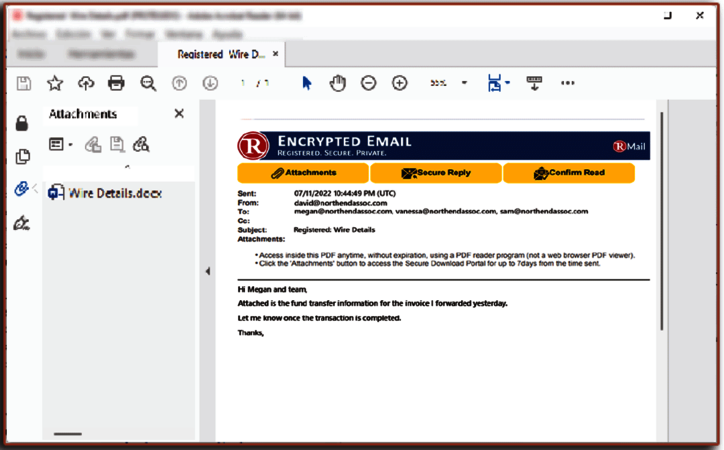
Compliance with GDPR and industry-specific regulations with Frama RMail
Automatic documentation for provable compliance
Across the globe, there are strict legal requirements for the protection of personal and sensitive data. Encryption emails with Frama RMail is a critical step in ensuring compliance with these data protection regulations, including the provisions of GDPR. With Frama RMail you receive a proof of delivery to demonstrate due diligence when it comes to compliance.

